Secure your data, secure your future
Don’t leave yourself vulnerable. In Time Tec can help you reduce your risk.
Don’t leave yourself vulnerable. In Time Tec can help you reduce your risk.



A methodical and controlled simulation of real-world cyberattacks conducted by our certified cybersecurity experts. It involves attempting to exploit potential weaknesses within your software systems, networks, and applications to assess their susceptibility to various cyber threats and or attacks.
A meticulous evaluation of an organization's IT infrastructure and software systems to ensure they comply with relevant industry regulations and security standards. These standards may include industry-specific mandates such as GDPR, HIPAA, PCI DSS, ISO 27001, or other cybersecurity requirements.
Finding and putting into practice a quick, automated, and adaptive cybersecurity strategy is the only way to prepare for what is ahead in 2023.
Cybersecurity protects your business from unauthorized access or exposure to data. We work closely with your internal security teams to protect and monitor your data so you can relax knowing that everything is taken care of.

Money, time, credit, and trust with your clients
We use penetration testing and monitoring tools to make sure you don’t have to compromise when it comes to protecting your data.
We don’t want you to lose any sleep over it
We'll make sure you're set up for success without insecurities or fears of losing to hackers.
From financial loss while ensuring you don’t lose data
Data loss is often associated with mass financial loss, but the biggest cost is the loss of your client’s trust.
Strengthening Defenses through Ethical Hacking: Pen Testing is a controlled and simulated cybersecurity assessment aimed at evaluating an organization's security posture. The primary objective is to identify potential vulnerabilities and weaknesses in an organization.
Understanding and Mitigating Cyber Risks: A threat model is a systematic approach used to identify and assess potential threats and vulnerabilities that may impact assets, data, and systems. By creating a detailed representation of potential threats, organizations can effectively prioritize resources to safeguard against attacks.
Identifying weaknesses before they are exploited: Our systematic process of identifying weaknesses and security flaws within an organization's IT infrastructure, applications, networks, and systems.
Possible Username Enumeration
Any user (hacker) can query the /api/common/user/get-all API and get information about other registered users in the application. This will allow the hacker to launch further attacks using the information from the response to this API.
Severity:
High
Confidence:
High
Evidence:
URLs:
Solution:
Ensure the proper access control is implemented for the API call, allowing only users with Admin role to access the users list.
Reference:
Strengthening Defenses through Ethical Hacking: Pen Testing is a controlled and simulated cybersecurity assessment aimed at evaluating an organization's security posture. The primary objective is to identify potential vulnerabilities and weaknesses in an organization.
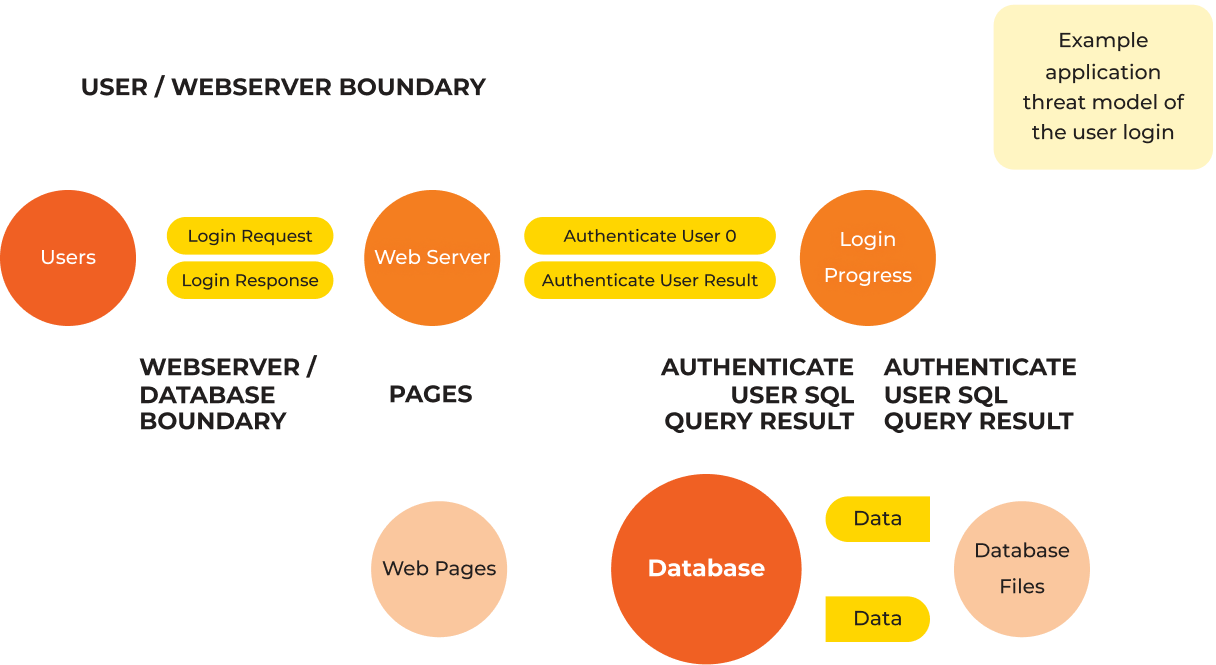
Understanding and Mitigating Cyber Risks: A threat model is a systematic approach used to identify and assess potential threats and vulnerabilities that may impact assets, data, and systems. By creating a detailed representation of potential threats, organizations can effectively prioritize resources to safeguard against attacks.
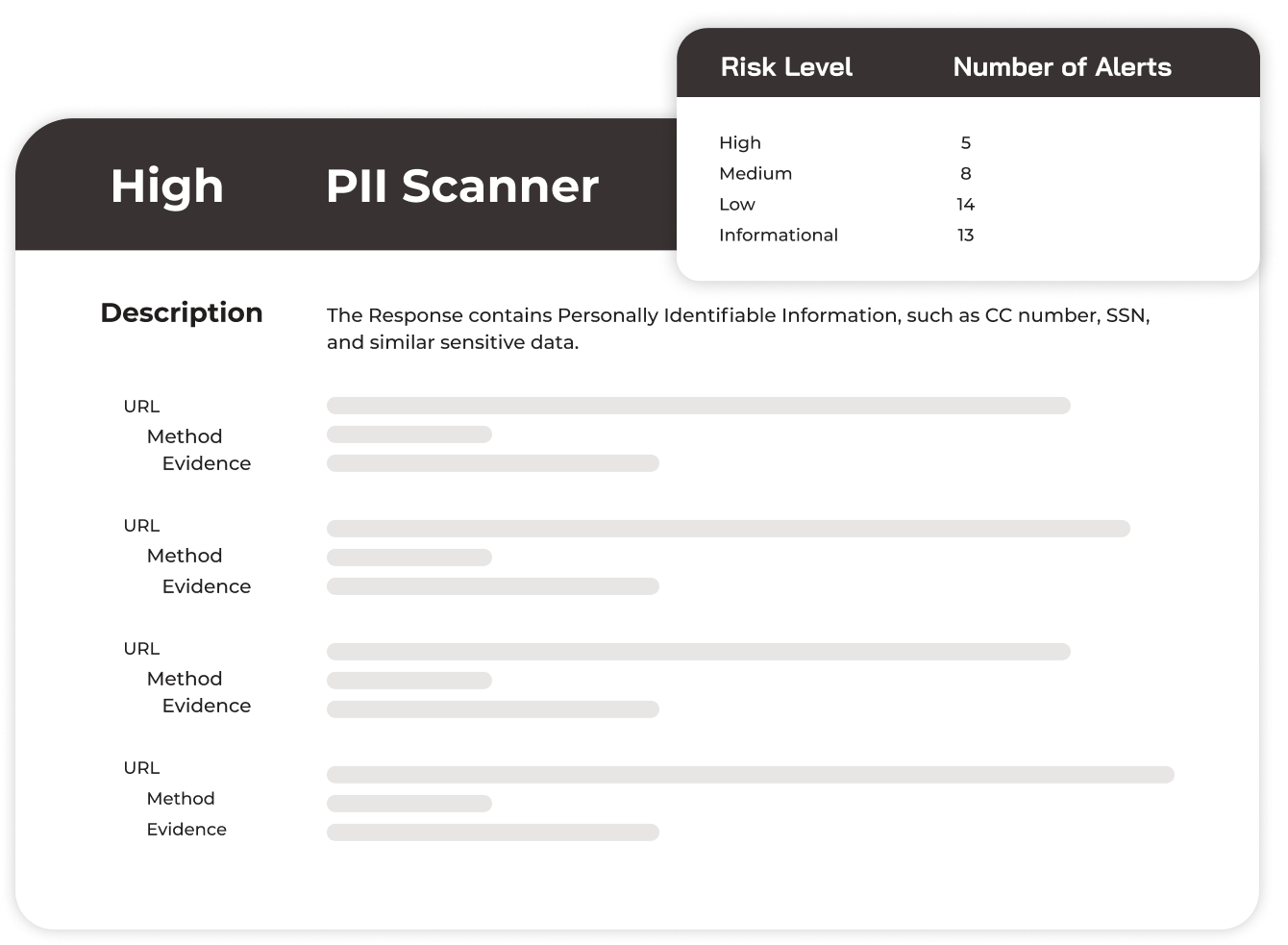
Identifying weaknesses before they are exploited: Our systematic process of identifying weaknesses and security flaws within an organization's IT infrastructure, applications, networks, and systems.

Our goal is to see you reach your potential.
We want to invest in your success, and we’re confident we can help you achieve your goals and provide a space for you to be more, do more, and have more.




































In Time Tec has been one for the value and the dollar amount that we paid for. This service has been top notch and well worth it. I would highly recommend the work and effort that In Time Tec has done for us. Truly, what we have now is a product that I love to share.
With any business relationship, you've got to get to know each other. I think In Time Tec is very unique about how they want to work with somebody and how they want to get to know someone. They are willing to put risk on themselves first and build the partnership and the trust.
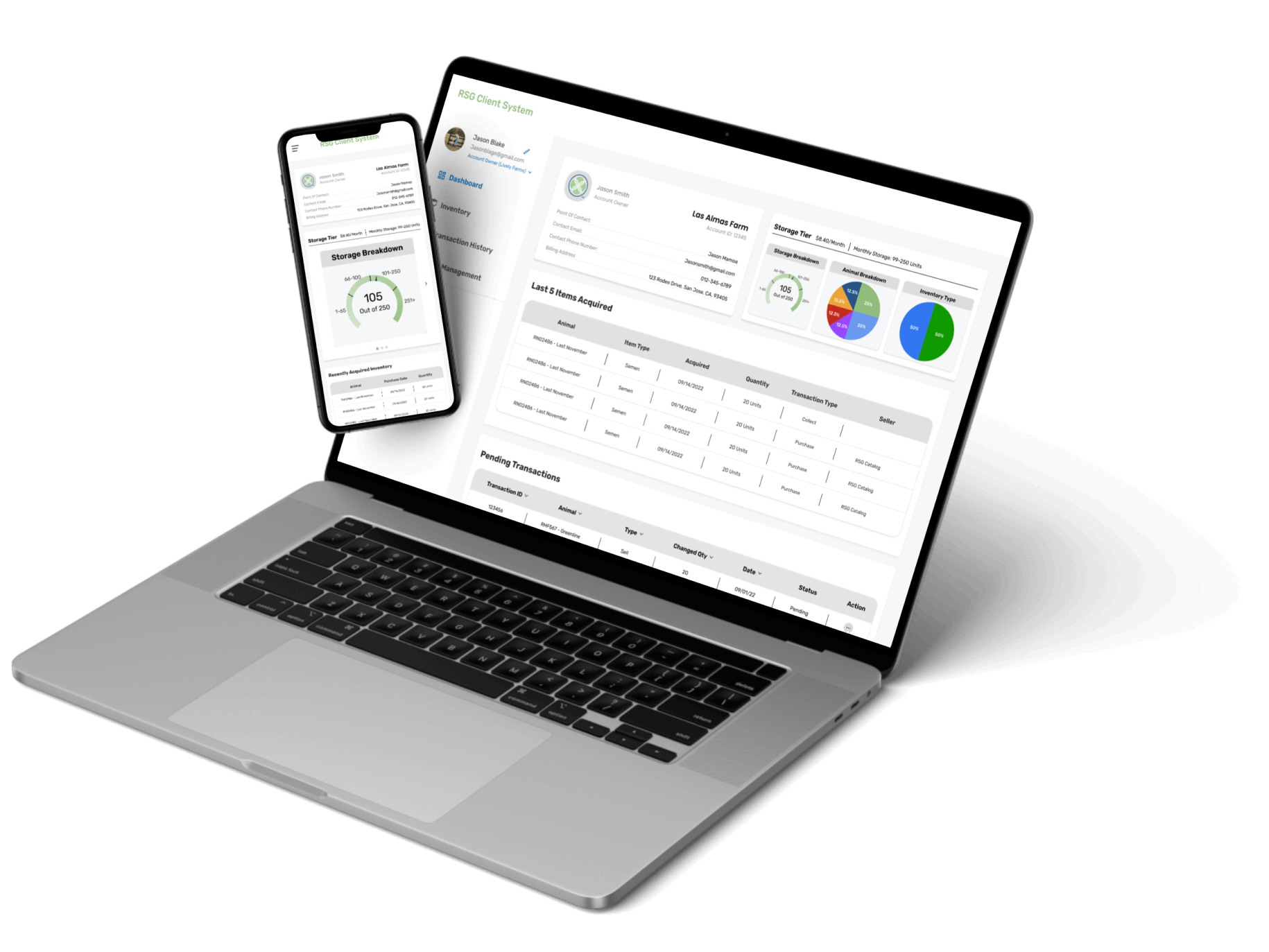
ITT was committed to creating efficient, innovative feedlot software and they delivered. From the start, it was clear they were dedicated to not only the success of our operation, but the industry as a whole. They created a suite of great products that’s going to really make a difference in the future of feedlots.
In Time Tec has been one for the value and the dollar amount that we paid for. This service has been top notch and well worth it. I would highly recommend the work and effort that In Time Tec has done for us. Truly, what we have now is a product that I love to share.
With any business relationship, you've got to get to know each other. I think In Time Tec is very unique about how they want to work with somebody and how they want to get to know someone. They are willing to put risk on themselves first and build the partnership and the trust.
ITT was committed to creating efficient, innovative feedlot software and they delivered. From the start, it was clear they were dedicated to not only the success of our operation, but the industry as a whole. They created a suite of great products that’s going to really make a difference in the future of feedlots.

When we think of technology, various integral parts of our daily lives come together. No matter how much we move forward with technology when it comes to secure personal information, people always rely on cybersecurity services. Let’s learn from scratch - what is cybersecurity?


